Fortinet Acquires Next DLP Strengthens its Top-Tier Unified SASE Solution
Read the release
Zero Trust security models are the gold standard of modern cybersecurity. Instead of assuming everything inside an organization’s network is safe, Zero Trust verifies access each time, regardless of the origin of a device or user.
Zero Trust is a security framework that challenges the outdated notion of perimeter-based security.
Organizations of all sizes can benefit from Zero Trust, but it can be challenging to implement a proactive approach if your organization still follows reactive strategies. The best way to implement this practice is to create policies aligning with the seven pillars of Zero Trust.
In this guide, we’ll explain Zero Trust security and its seven principles. Ensure your cybersecurity strategy touches on all aspects of Zero Trust to reduce your attack surface.
In this article:

Zero Trust is a cybersecurity model that operates on the principle of "never trust, always verify."
Unlike traditional security models that assume everything within the network is trustworthy, Zero Trust emphasizes that no entity, whether inside or outside the network, should be trusted by default. The system verifies every user and device, every time, before granting access to any resource.
Embracing a Zero Trust approach helps organizations:
Zero Trust is a significant shift in cybersecurity practices. It emphasizes continuous verification and strict controls to protect dynamic IT environments from increasingly complex threats.

Zero Trust architecture emphasizes several key components to ensure robust security.
These elements work together to create a comprehensive security framework that assumes no trust by default and continuously verifies every access request, regardless of its origin or destination within the network.
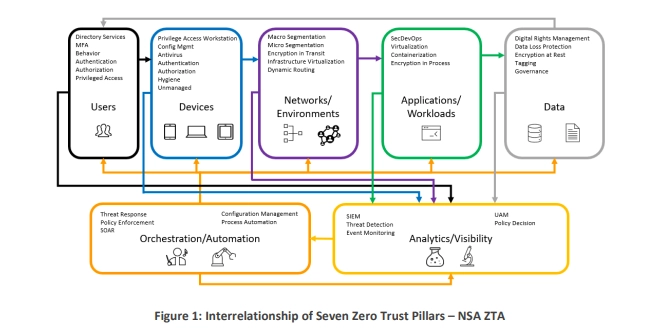
The Zero Trust model is effective because of its comprehensive and proactive approach. To protect your digital environment, follow the seven pillars of the Zero Trust framework.
This pillar emphasizes the importance of verifying users' identities and ensuring they have appropriate access to resources—not only for your remote workforce, but for all access requests originating from inside and outside the network.
Multi-factor authentication (MFA), single sign-on (SSO), and identity governance ensure that only authenticated and authorized users have access to sensitive data and systems.
Implementing least privilege access ensures that users and systems are granted only the minimum necessary permissions to perform their tasks. This minimizes the risk of privilege escalation and limiting potential damage from compromised accounts.
Devices accessing the network must comply with your organizational policies. Zero Trust device security ensures this by continuously monitoring devices, applying patches and updates regularly, and ensuring endpoint protection measures are in place.
Every device connected to the network must be identified and authenticated before being granted access. This can be done through methods such as device certificates, biometric authentication, or multi-factor authentication.
Additionally, devices must meet certain security requirements and comply with company policies before being allowed access to the network. This includes having up-to-date software patches, strong password policies, and encryption protocols in place.

Micro-segmentation and least privilege access are critical components for securing workloads and protecting sensitive data from unauthorized access in both cloud and on-premises environments.
Micro-segmentation involves dividing networks into smaller segments or zones, effectively limiting lateral movement of threats and isolating workloads.
These security measures provide organizations with granular control over their network and data, enabling the enforcement of robust security policies and protection of sensitive information. Network security also involves implementing:
These actions minimize attackers' potential for lateral movement within the network, reducing your attack surface.
Organizations must protect applications and workloads from unauthorized access and vulnerabilities. Workload security refers to digital processes and IT resources (both public and private) used in the course of business operations.
This Zero Trust pillar includes security measures such as application whitelisting, secure coding practices, regular vulnerability assessments, and web application firewalls (WAFs).
Protecting data involves encrypting data at rest and in transit, implementing strict data access controls, and continuously monitoring data access and usage.
Data loss prevention (DLP) solutions like the Reveal Platform by Next also protect sensitive information from unauthorized access, including insider threats.
Continuous monitoring and real-time visibility into network traffic, user behavior, and system activities are vital for identifying potential threats and anomalies.
Advanced analytics, including user and entity behavior analytics (UEBA), security information and event management (SIEM) systems, and artificial intelligence (AI), detect and respond to security incidents.
Automation plays a crucial role in enhancing the efficiency of security processes within a Zero Trust architecture. By implementing continuous monitoring systems powered by artificial intelligence, organizations can detect anomalies and maintain vigilant oversight of access control and data visibility.
This automated approach allows for real-time identification of potential security threats and streamlines incident response procedures.
Automation and orchestration are fundamental components in deploying a comprehensive Zero Trust model across an organization's systems. These advanced techniques enable seamless integration of security measures, reducing manual intervention and minimizing the risk of human error.
Although cyber threats are becoming more advanced and pervasive, the Zero Trust model is a reliable framework organizations can use to bolster the security of sensitive data. You can’t prevent all breaches or data loss, but following the seven pillars of Zero Trust will set your organization up for success.
Instead of manually managing Zero Trust policies, opt for a platform that integrates everything in one simple dashboard. Reveal provides end-to-end data visibility and protects it at every turn, from SaaS solutions to email. Book your Reveal demo now.
Switching to a Zero Trust model has many benefits, but it does present several challenges, including:
Yes, organizations should apply Zero Trust to cloud environments. As organizations migrate to cloud services, Zero Trust tightly controls and continuously verifies access to cloud resources.
This approach protects against unauthorized access and data breaches in the cloud, which is essential for balancing the cloud's availability with security.
Automation streamlines Zero Trust principles and improves response times. It makes Zero Trust actionable for both small and large businesses, automating workflows and incident response playbooks to address threats quickly.
Automation also ensures consistent application of security measures across the network, reducing the risk of human error and enhancing overall security.

Blog

Blog

Blog

Blog

Resources

Resources

Resources

Resources

